Healthcare IoT Security: Risks, Rules, Best Practices, and Our Advice

The Healthcare industry has made a significant qualitative breakthrough with the development of IoT. But in order to provide quality care to patients, the technological side must be secure enough. Paraphrasing a well-known aphorism, healthy security software in a healthy IoT system.
Based on numerous cases of hacking systems and theft of sensitive data in hospitals and health centers, the importance of establishing reliable protection becomes obvious, which 95% of the polled healthcare organizations agree with. Let’s learn in detail what threats IoT medical device security gaps can pose and how to protect yourself from the consequences. If you shoulder responsibility for a private or state healthcare organization’s cybersecurity, this article will be just what the doctor ordered.
Security reports for IoT healthcare
The healthcare IoT market has shown rapid growth in recent years, which is facilitated by two points. Firstly, the increased availability of high-speed Internet creates favorable conditions for the work of many interoperable devices in a single network. Secondly, reducing the cost of sensors gives a huge impact on the popularization of health devices. The combination of factors from the innovative nature of medicine, as well as the development of the IT sector and AI, form a clear picture of the highly promising synthesis of IoT and the healthcare industry, which market share is expected to reach $411 billion by 2026.
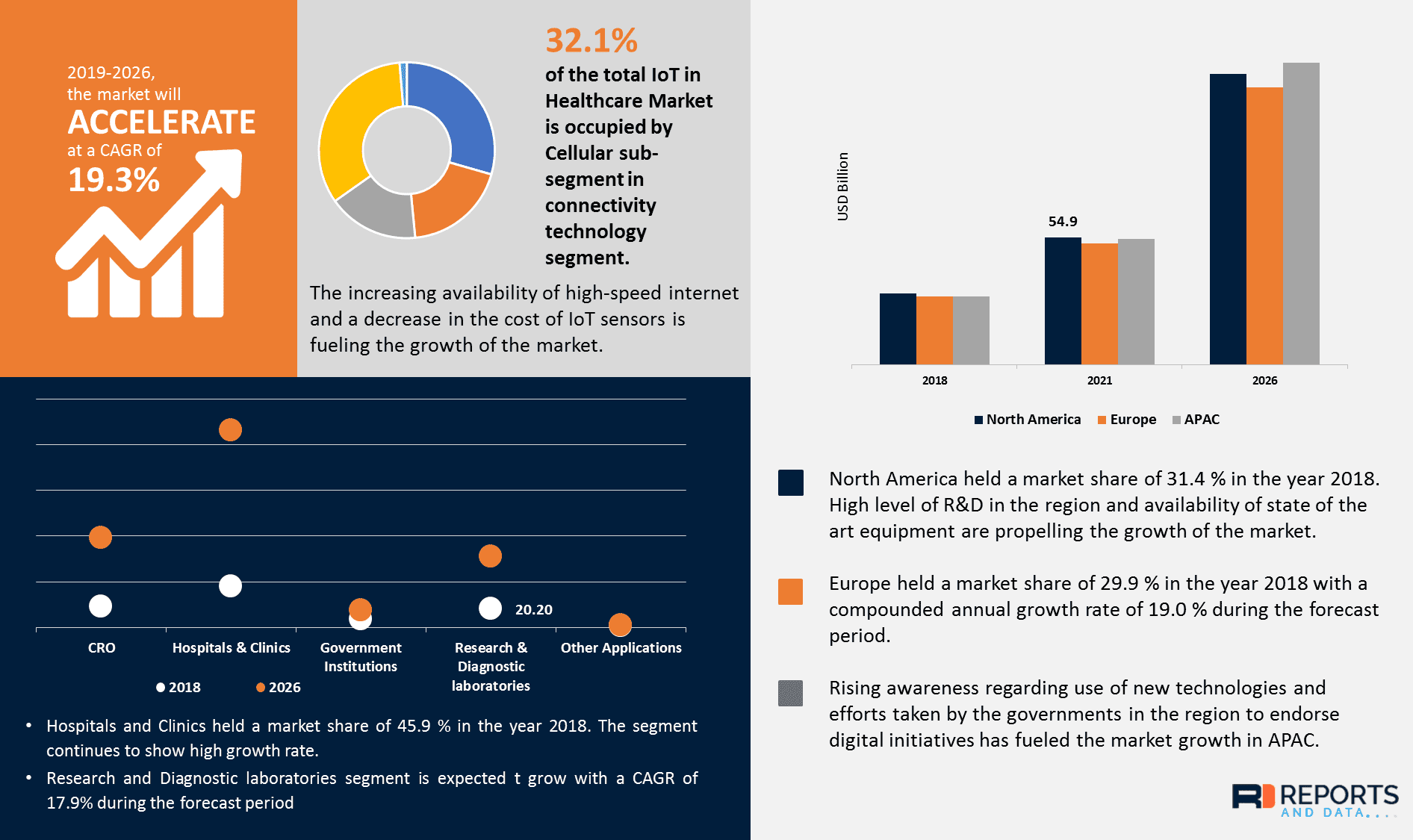
Reports and data
A large-scale spotlight report from Vectra for 2019
indicated the widespread adoption of health IoT devices, which, against the backdrop of network segmentation and access control lack, as well as dependence on legacy systems, creates positive conditions for cybercriminal attacks. The report says that most medical device IoT security breaches do not come from outside interference, but from within (59% vs. 42%). In other words, human error causes threats more often than the targeted actions of attackers.
The main priority for healthcare organizations is to protect patients and their personal information, which means more thorough work with hardware and software developers on security and privacy issues with IoT in healthcare. For optimal protection, you need to understand the types of threats your product may face. Without further ado, let’s look at the most common ones.
Learn more about IoT healthcare in our recent blog post
What challenges await IoT security in healthcare?
During the years when hospitals were adopting the Internet of things, several major healthcare IoT security challenges have come to the surface:
-
Hardware
To begin with, IoT hardware includes a broad spectrum of devices such as sensors and wearables. Each IoT hardware consists of the following building blocks:
-
“Thing” (the asset you want to control);
-
Data Acquisition Module;
-
Data Processing Module;
-
Communication Module.
Security and privacy issues with IoT in healthcare are multiplying every day. First of all, it is a threat to outdated hardware. As the efforts of manufacturers are aimed at mass production of new models, the safety is simply sidelined. This leads to the fact that many devices are not updated according to the latest IoT security requirements, and after a while attackers can find vulnerabilities that have not been covered by fresh patches.
Another potential IoT hardware threat to hospitals is that a microchip can be injected with the malicious circuit at any stage of creation, even after successful fabrication. In this case, sensitive data may leak, and important system mechanisms may fail.
-

Trendmicro
-
Network segmentation
Segmentation is a key for the implementation of a quality security strategy. Splitting a network into subnets is a popular way to improve performance and medical IoT security in an organization. Network segmentation allows you to divide traffic into external (guests and external users) and internal (authorized users).
The lack of it can lead to the fact that a locally implemented device can have a negative impact on the entire organization when moving patients’ sensitive data.
Without a network segmentation, a hacker can easily take control of misconfigurations within an organization. For example, see any server or workstation that is connected to an internal network to look for additional access.
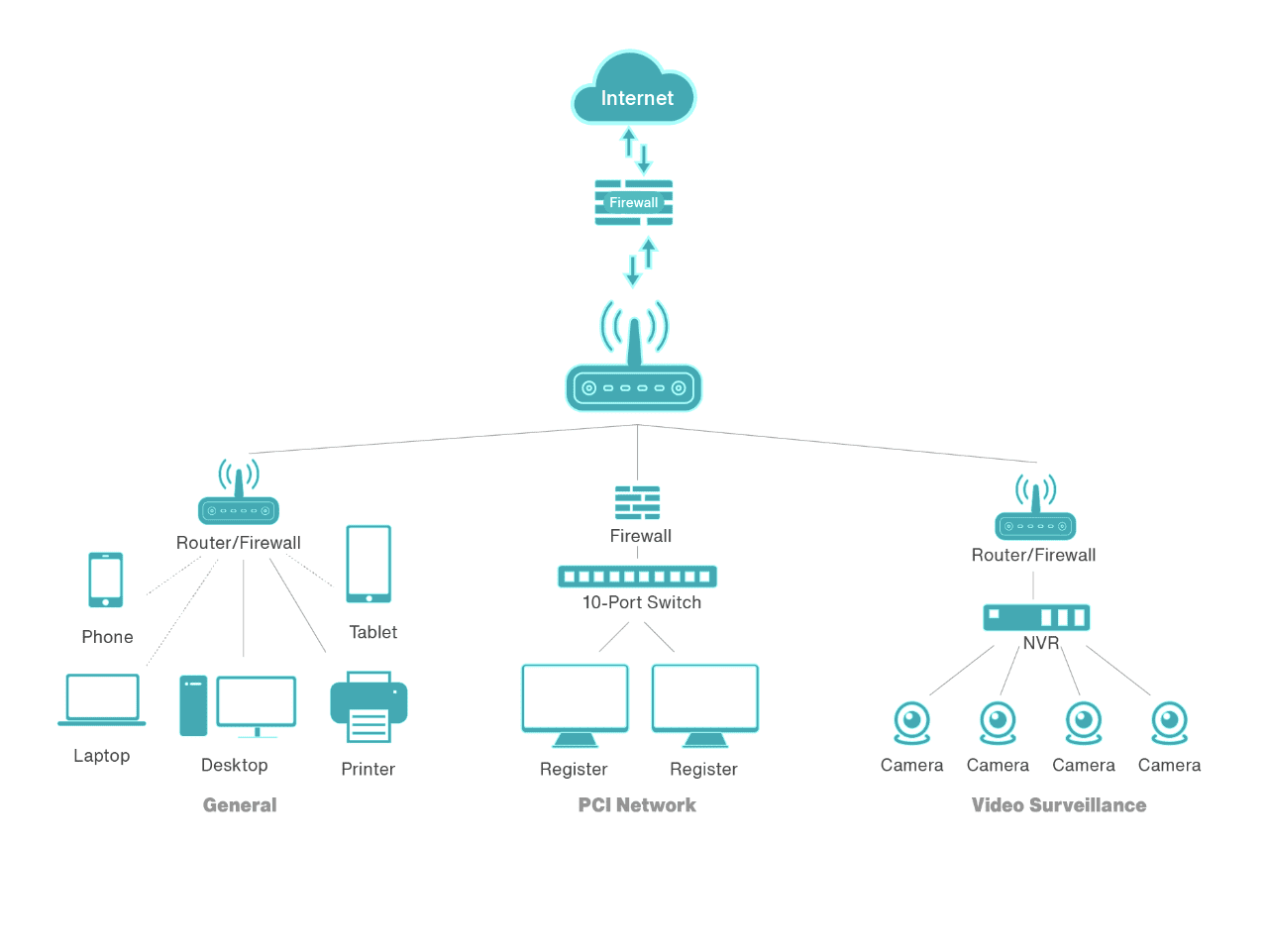
Image 3. Network segmentation for small-business. Source:
hikvisionTo achieve network segmentation, you need to:
-
identify all incoming devices using Network Access Control;
-
differentiate the IoT segment from other networks;
-
establish the effective operation of an automated security framework to protect the network.
-
-
Legacy systems
This issue stems from the specifics of the work of hospitals. Patching and updating systems is often an unaffordable luxury for them, as this interferes with the provision of patient care, which is required 24/7. Thus, hospitals are forced to deal with legacy Windows XP or MS-DOS systems, which increases the number of IoT security breaches and vulnerabilities by several times. In this case, hospitals will lack security updates and important cybersecurity controls, which will greatly facilitate the work of attackers.
Socket3
-
Ransomware
Ransomware is a type of malware that blocks the user’s access to the device and its content, after which it requires an online payment to restore access. Once the most popular security threat in healthcare, now ransomware has fallen into the shadow of the newer risks and human errors. Despite this, security companies note the importance of constantly monitoring your level of protection to prevent ransomware attacks.
Successful protection is possible if your organization uses endpoint security software in addition to antivirus, provides regular backups, ensures proper access management, and has a recovery plan. If such an attack is not prevented in time, the hospital will go offline for a long time, and its work will stop.
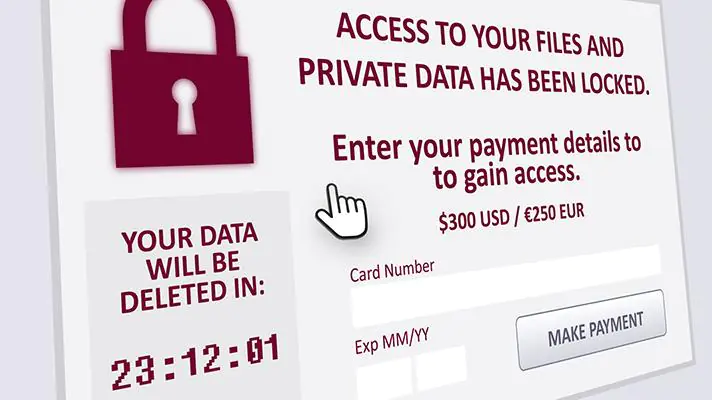
Healthcare IT news
-
Medjacking
Medjacking is a type of security threat used for implementation in a medical device in order to gain access to its software. The medical industry started talking about the threat in 2015 after a TrapX report, which revealed the vulnerability of all healthcare organizations to hijacking medical devices, namely the infusion pump, which inject drugs directly into the patient’s blood. Attackers could hack the device and manually kill people.
In addition, medjacking can infect devices with various malware to steal confidential information. In the same 2015 year, it was decided to abandon all devices with vulnerabilities in the United States. Today, it is still important to carefully select and verify medical devices from suppliers.
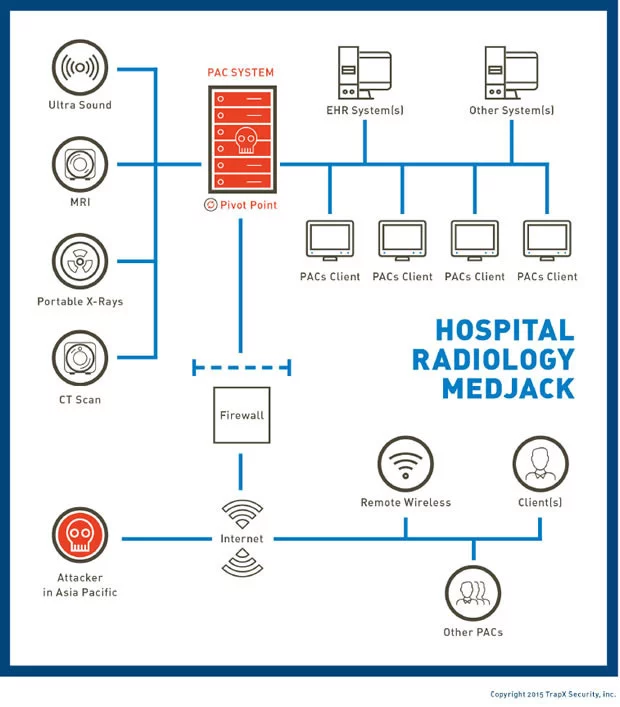
Computerworld
Knowing the common industry challenges, let’s move on to considering a list of vulnerabilities that you need to know in order to establish the optimal level of cyber security.
The most vulnerable areas
We can distinguish the following areas for the entire industry:
-
Debug port
Debug port exists in a device to facilitate the development or debugging. It can be either hardware or software and is usually not removed to avoid additional costs due to design changes. That is why when an attacker connects to a virtual or physical debug port, it becomes possible to read, high-jack, or modify the firmware. Moreover, it is beneficial for attackers not to steal but ensure that firmware is as old as possible so that it has healthcare IoT security holes that can be exploited.
Physical devices may, in some cases, be insecure, which means some models can connect to a specific port using special commands without authentication. If an attacker manages to gain access to these commands, for example, by using hardware attack, medjacking or reverse engineering, they will be able to crack devices.
A vivid example was the routers of well-known brands D-Link and Cisco, which had an unprotected debug port for firmware, that made it possible to intercept outgoing traffic from there. Through diagnostics, the port makes more than 90% of hacks, so its protection is a priority. You must have some authentication and authorization system (pin code or password) to determine if it is yours/someone else’s. Also, take care of the ability to completely crop the rest of the world so that you can connect to the router through its own Wi-Fi or patch cord.
-
Interception of insecure traffic
When transmitting information to the hospital’s IoT system, there is a risk of confidential data interception. To obtain it through a stream of unprotected traffic, the attacker must be physically close to it or plant a beacon like a Raspberry Pi that would read the medical data with sensors and send it to the server.
Another hacking option is to connect an additional user in order to pair devices for data draining. It is possible to prevent data theft by providing pairing with such physical and software methods that will prevent attempts to switch to other devices. Besides, the risk of data interception increases with a lack of network segmentation and the use of legacy systems.
-
Authentication and authorization
Authentication and authorization should be presented at all stages of interaction to ensure protection against hacking attempts. Both of them are needed when the device contacts the data transmitter, and when the latter interacts with the aggregating server. Your infrastructure must be protected at the data transfer level to prevent any access from outside.
In general, IoT medical device security is individual for each digital ecosystem, so if you want to find out or create a safe environment for your healthcare software development agency, we are ready to help and provide more detailed information.
If your system has been hacked any of the above methods, you should know where to look for traces of intruders. Pay attention to the most common areas of hiding suspicious activity:
-
HTTP tunnels
This case is inherent in the most common methods of attackers to hide command-and-control communications in the healthcare institution network. Traffic is hidden under the guise of encrypted web traffic, being, in fact, external communication with multiple sessions over long time intervals. Hackers often pass connections off as the traffic of the Internet provider and hide them in HTTP tunnels. Two things serves as an obstacle in identifying the correct operation of the device:
-
the provider sets its own requirements;
-
the documentation often trails behind upgrades and versions.
-
-
DNS tunnels
A number of data theft methods can be performed through DNS (Domain Name System) tunnels:
-
using the reputation of DNS tunnels as security tools, attackers hide exfiltration of data using DNS tunnels, which is the most standard crime method in DNS tunnels.
-
since in hospitals the data traffic is high, — due to sharing records of patients and medical devices management, — a lot of traffic can come, which is used by cybercriminals. They commit the “smash and grab“ crime by sending large packets of data in a short period of time in the direction of unused external destinations.
-
devices become vulnerable at the time of medical information transfer, which may result in data smuggling behavior. This happens according to the following scheme: the internal host provider requests a large amount of data from internal servers and then transfers it to the external system, making data smuggling possible.
-
Who will be responsible?
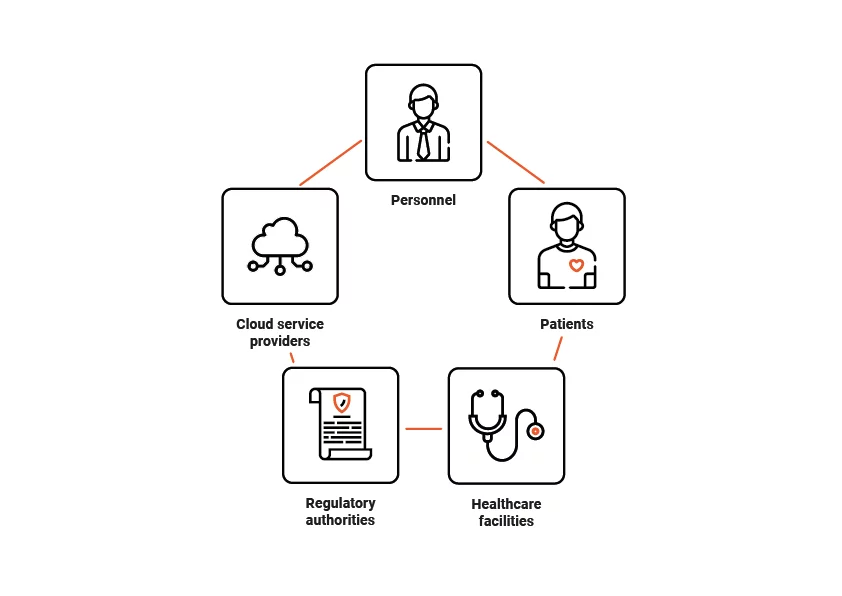
As the issue of patient data is of utmost importance and protected under regulatory compliance, let’s find out who is responsible for the medical ioT security system at any healthcare facility.
-
Employees
Workers deal daily with software and devices, so you need to educate them on the proper use of medical gadgets. For example, do not use devices with a browser to surf the Internet or watch videos, so that not infect them with viruses.
-
Patients
Healthcare facilities often allow people to bring their own devices (BYOD). This is a convenient solution for patients, but it can cause security breaches and vulnerabilities. This is caused by the mismatch of personal devices with security requirements, which is why attackers can gain access to sensitive data not through IoT medical appliances, but through personal patients’ or employees’ devices.
-
Healthcare organizations
With the increasing connectivity of medical gadgets, there is an elevated need to pay more attention to security and privacy issues with IoT in healthcare. Healthcare organizations are required to monitor devices that are reachable via the internet for possible threats and malware, as well as monitor the latest software. When updating medical device IoT security, you should carefully check that this does not cause conflicts in the system and does not harm the patient indirectly.
-
Cloud provider
While healthcare organizations take care of secure storage and encryption of data, cloud service providers fill the gap in data access and transmission control. Depending on the number of devices connected to the network, an increasing security risk occurs, and it is providers who can monitor the processes of admission and data transfer.
-
Regulatory authorities
In order for Personal Health Information (PHI) to be securely stored and transmitted through IoT devices, regulatory bodies must ensure reasonable and clear legislation.
Check out healthcare case story in our portfolio
How to secure IoT healthcare software and devices: best practices
We discussed who will be responsible in certain cases of your system infection above. But everyone will agree that it is in our interest to completely avoid such an accident and prevent the penetration of malicious threats. Thus, let’s discuss the best solutions on how to protect your IoT healthcare environment.
Top Solutions for IoT Healthcare Cybersecurity
-
General solutions
-
Full control of your network
Managing your network is the primary means to control the visibility of the network, i.e., monitor it for breaches to reduce risks. The network has intelligence, scanners, and a set of various solutions for providing the highest quality protection against cyber attacks.
Optimal network control is facilitated by providing network segmentation. The essence is that it allows you to transfer data only in the redistribution of authorized users. The sensors transmit data to the server via Bluetooth, which then transmits it via the HTTP channel to the server. Thus, even in the case of data interception by intruders, they cannot decrypt it without a key. Subsequently, the server transfers data to the database, which access must be from within the organization. In other words, to achieve high-quality IoT security of your network, each element of the system must be protected at its own level.
-
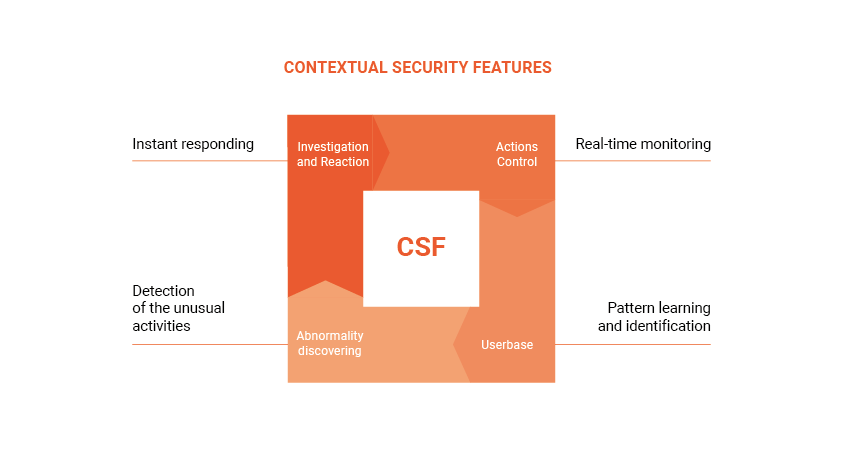
Contextual security
Your platform should possess contextual security for several reasons. Thanks to this type of security, IoT solutions can be isolated in their own network at the time of need, where you can configure policies to monitor suspicious activity (e.g., attempts to intercept data) or even traffic patterns. For the IoT network, the advantage will be the installation of additional thresholds and filters for increased security. Thus, for example, if DDOS (distributed denial-of-service attack) is noticed, it can be overcome with partial or entire closure from the network.
-
-
Connected devices segmentation and centralization
When working with connected devices, you should create a separate network to monitor them carefully. Segmentation and centralization of devices will allow achieving flexibility in their control, giving the opportunity to alternate these methods depending on the threat. It makes sense to use IoT aggregation hubs for further device control.
Remember that you always need to know what the devices have access to. The conditions for data storage and access to PHI/PII (Protected Health Information/Personally Identifiable Information) will determine their IoMT security policy settings.
-
Test and visibility maintenance
The connection of new devices to the network will require you to be as agile as possible not least because of the possibility of hardware infection that we mentioned above. The wireless architecture will help you monitor and manage their ongoing emergence. The complexity of monitoring depends on the number of devices connected to your network. It is important not to lose sight of them and set up a quality monitoring platform from the very beginning.
-
Technical solutions
-
Hardware solution
The consequences of the malicious threats penetration into hardware can vary from disabling personal devices to interferences in the operation of transport and defense systems, which can become disastrous. In order to avoid hardware hacking, the debug port of the device must be hard to access, and can be additionally protected by an electronic digital signature. As a preventative measure, the process of testing and detecting infections should include activities from detecting random flaws to thoroughly hidden and intentional ones.
A positive impact on the security of hardware can be a change in the design process by limiting information and selective provision for those who are involved in certain developmental processes. To counteract the negative effect of infection, monitoring processes should be implemented in the chips to track suspicious behavior followed by the immediate quarantine if necessary. Finally, do not forget about providing HIPAA (Health Insurance Portability and Accountability Act), HITECH (Health Information Technology for Economic and Clinical Health Act), NHS (National Health Service), and FDA (Federal Food, Drug, and Cosmetic Act) compliance for IoMT security.
-
Encryption and cryptography
Cryptography can be implemented for counteracting data interception in the IoT environment on both software and hardware levels. However, in the case of the latter, it will be much more challenging. Traditionally, lightweight cryptography (LWCRYPT) is used as cryptography techniques for smart objects in IoT. Among the types of LWCRYPT techniques, you can use asymmetric and symmetric ones:
-
asymmetric — uses two keys for encryption. The public key is accessible to all, and the owner has the second private key. Usually, asymmetric encryption is used only to establish a handshake, the so-called key exchange, during which public and private keys are exchanged between the sender and the recipient. Then symmetric encryption takes over the main work.
-
symmetric — the simplest encryption technique. It uses one secret key (including number, word, character set, or even symbols not available on the keyboard layout), and created during the session, after the handshake. The sender and receiver must know the contents of this key to decrypt.
Such hardware solutions as various devices and sensors store asymmetric keys in themselves to create a secure connection in the form of an HTTP tunnel between the sensor and the consumer.
In order to cope with the complexities of the insecure encrypted IoT network, an authentication pattern for implantable healthcare devices has been created to replace traditional passwords. This way, the use of ultraviolet light allows you to seal encrypted keys in the patient’s body.
-
-
Trojan and Malware solutions
There are several malware protection methods that you can use successfully:
-
Signature-based detection is the most common method dependent on an antivirus system signature. Signatures are checked in the database, and when no similarities are found, malware is detected. This method is not suitable for devices with a small amount of memory.
-
Static methods are based on the static characteristics of the device. The common static analysis searches for malware without the actual code change, using various tools for identification and collection of simple signatures. It is lightweight and low in resources but limited in verification.
-
Unlike static, dynamic detection determines malware by analyzing suspicious activity, which includes CPU load, network behavior, virtual memory, calls, SMS. The perfect way to protect is considered combos static and dynamic detections.
By isolating IoT health services from other apps in a secure environment, you can achieve reliable protection against malware such as medjacking. Another way is to create a hub of independent devices and connect them to healthcare service providers. An example of such a hub is the wristband device Amulet, which contacts a smartphone before establishing a secure connection with a healthcare service provider.
-
-
EMI and side-channel attacks
EMI or electromagnetic interference issue becomes more relevant every year as our life becomes more dependent on electronic devices. EMI attacks send electromagnetic waves to devices, which cause a discrepancy in their operation. The most effective way to deal with EMI is shielding and filtering. They are able to increase resistance before EMI.
Shielding surrounds the object with a metal plate to block electromagnetic pulses, upon contact with which they are scattered in different directions. Thanks to filtering, the necessary noise and interference are passed through the electric current in the conductors, while unwanted distractors are eliminated. The mix of shielding and filtering can detect abnormal sensory signals.
We have come this way with you from clarifying the complexities of medical IoT security to reviewing the best security solutions. It’s time to take stock.
-
Conclusion
Each doctor will tell you that in order to help patients, you need to be healthy yourself. The same is true for IoT security in healthcare: IoT is an organism of the hospital, and the security is its immunity. Only a system with healthy immunity can withstand external threats like viruses. Contact us to take care of your system’s security so that it subsequently takes care of your patients.
Frequently Asked Questions
What are the main challenges in IoT security?
- hardware;
- network segmentation;
- legacy systems;
- ransomware;
- medjacking.
Each challenge can arise in certain conditions and have several solutions. Find out more in the “What challenges await IoT security in healthcare?” section.
What vulnerable areas does IoT technology in healthcare have?
- debug port;
- interception of insecure traffic;
- authentication and authorization.
Are there any tips on how to protect IoT software and devices?
- full control of your network;
- contextual security;
- connected devices segmentation and centralization;
- test and visibility maintenance.
To know more about technical tips and tricks, feel free to read the ”How to secure IoT healthcare software and devices: best practices” section.




